OIX Members â please login to view this page
 Latest Document[-]
Latest Document[-]




 Latest Events[-]
Latest Events[-]General Area: General area
 Latest Advisory Board[-]
Latest Advisory Board[-]
Don Thibeau served on the Board of the OpenID Foundation, a non-profit, standards development organization after he was OIDF’s Executive Director for 10 years. As founder of the Open Identity Exchange, he led OIX for 10 years and recently served as its Vice Chair. Open Identity Exchange is a a non profit organization developing scheme rules, trust frameworks and governance for identity systems at scale. Early in his career, Don led business development and strategy at the LexisNexis Group...
Richard is a Senior Policy Advisor for the FLA, specialising in fraud related issues within consumer credit, anti-money laundering and a number of other key issues for the consumer credit industry. He is also on the main Board and Editorial Board of the UK’s Joint Money Laundering Steering Group (JMLSG).
Phillip is Director of Digital Technology and Innovation at UK Finance, the trade body for the financial services industry. His portfolio includes digital identity, payments innovation, new digital money and open banking/finance. Before that, Phillip worked at Payments UK on payments regulation and strategy.
He has a public policy background – at the Local Government Association leading on local government finance and public service reform. Before that at HM Treasur...
Jonathan is an industry veteran who joined the Payment Systems Regulator in January 2021 as an expert advisor on payments processing, fraud prevention and identity management. He works closely with colleagues in policy development to support the PSR’s three statutory objectives of choice and availability for service users, competition, and innovation and development of payment methods.
<...
Luella assists with the Policy and Regulatory Affairs work at the BGC, including leading on Safer Gambling Week.
Luella joined the BGC in July 2021 as a Policy Officer after graduating from the University of Bristol with a degree in English Literature and Philosophy.
 Latest Banner Settings[-]
Latest Banner Settings[-] Latest FAQ[-]
Latest FAQ[-]
Please visit our “About” & 'Find out More' pages.
Join HERE
OIX encourages membership from all elements of the ID ecosystem.
If you are a provider of identity services or a representative of an organisation that relies on verified IDs within its business processes, your input into the development of our guidance on trust frameworks and interoperability will be hugely valuable.
Whether from the public or private sector, a regulator or trade association, media or analyst,
Open market models underpin the development of a sector that is innovative, competitive and focused on user needs. This includes:
More choice for eCommerce and product managers about the policies that they apply to user interactions.
Market pricing for products and services across the entire identity infrastructure.
Economies of scale as service standardization lowers costs for all parties
A more inclusive approach as the needs of diverse users are actively con...
Yes, the key challenge to providing identity assurance at scale is removing the need for direct trust agreements between ID services providers and those who rely on IDs for their business processes. OIX is a membership community for all those involved in the ID sector. Vendors and clients, regulators and influencers connect and collaborate to develop the rules, tools and confidence to create Trust Frameworks for identity in order to accept universally trusted identities.
 Latest Home Page Links[-]
Latest Home Page Links[-]
Digital ID is set to improve how people access any kind of service. In some countries, like Denmark, it’s now the primary way people access both public and private sector services. However, some people do not want a digital ID and are worried that it will not be a choice.
The simple answer is that digital ID will not be mandatory. There will always be choices.
One of the reasons for this concern is the fact that many people already struggle to ...
OIX will influence how Digital ID will evolve to make sure it meets current and future needs. Join OIX as a member to work with us to make Digital ID a success. Our working groups are where we collaborate to shape the future of Digital ID.
Is there a scheme in your sector? If not, start one! OIX can help bring together expert organizations in your sect...
Digital ID Jargon Explained

The identity industry, just like any another industry, loves to use its own specialist terms. This often causes confusion as every term with broad meaning may have a specific definition in the identity ecosystem. This list of terms and their identity industry meanings should help bring clarity in this space. More information...
Digital ID provides you with continued access to the latest ID proofing techniques and credentials. ID Providers will continuously innovate to ensure they maintain their customers, end users and organizations like you.
Digital ID balances the following fundamental needs of a service provider:
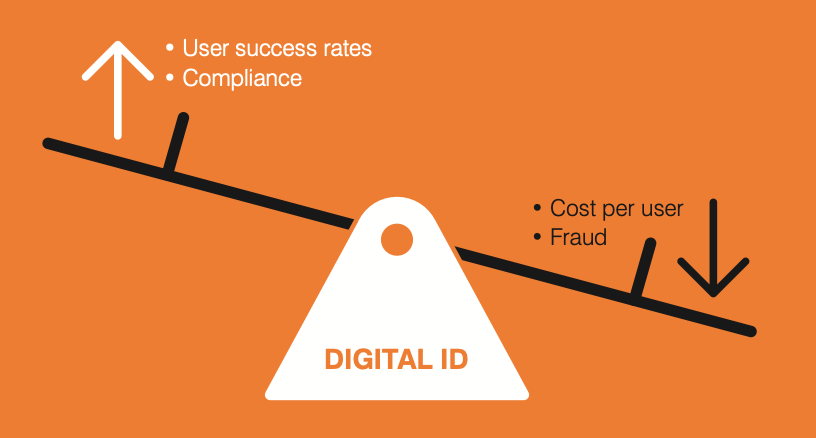
There are a number of key stake...
 Latest Leadership[-]
Latest Leadership[-]
Gareth Narinesingh is a digital identity evangelist with a strong conviction that reusable identity will transform peoples’ lives for the better. He has recent experience of digital identity sales and product management and before this built his career in regulatory consulting, FCA supervision and various market roles in banking. Gareth’s key objective is to work across the OIX members...
Paul is focused on developing a perspective as to how Mastercard engages with and enables reusable identity ecosystems globally which includes working with regulators and industry partners across the globe. He serves as a subject matter expert in authentication and reusable identity and helping support bringing this new opportunity from theory into the real world. He is responsible for ensuring that M...
Sophie is a DPhil student at the Oxford Internet Institute and a freelance researcher. Her doctoral research examines how normative conceptions of citizenship embedded in government digital identification platforms shape access to rights, resources, and political participation. Sophie has also conducted freelance research wit...
OIX PR Manager
Highly experienced communications professional with over 20 years of experience in developing and delivering strong strategic communications programmes. I have worked directly with leadership teams, managing expectations and securing support, while mapping out communications strategies aligned to commercial objectives.
 Latest News[-]
Latest News[-]- New research by Open Identity Exchange (OIX) and ...
Before any of us can access the products and services that we want, we have to prove who we are and that we are entitled to those products and services. Digital ID is changing how we do this for the better.
But too many of the people who will be able to use digital ID to access the services they are entitled to, still do not know what digital ID is or how it will work. It is a confusing subject, b...
All businesses are going to be able to benefit from digital ID in one way or another, regardless of the sector they operate in - finance, property, telcos, insurance, legal, travel, employment, gambling and any age restricted services. It will be a gamechanger for organisations that use it to onboard and allow customers access to their services.
However, digital ID is complex and confusing. Ther...
Videos aim to address the lack of understanding and trust among general public about
digital ID, to highlight exactly how it will work and how it will benefit them.
...
It is becoming more urgent that organisations take steps to understand
how digital ID will impact them, says OIX.
UK, 16th January 2024 – The
 Latest Project & Paper Policies[-]
Latest Project & Paper Policies[-]
A project may be formed (sponsored) by any member of OIX in collaboration with one or more other members. Non-member organisation may collaborate on an OIX project. All non-members are required to sign the OIX Participant Agreement (Link) to protect IPR.
There are three ‘costs’ associated with running an OIX project: Participation fee, Facilitation Fee and Project Funds.
Participation Fee: All participating organisations will pay a ‘part...
At all times, participating members and non-members in projects and white papers must observe the Code of Conduct.
This policy is to set out the principles by which OIX projects should be formed, governed and executed with the intent of achieving a desirable outcome and to set out the principles relating to the publication of white papers. The objectives are to ensure OIX Projects:
- Further Identity
- Are clearly aligned to the OIX’s vision, mission and objectives
- Are effectively managed within the limitations of the scope, resources...
A Member paper may be written by one or more OIX members. It should reflect a current issue or opportunity that is relevant to the purpose of OIX and is to further identity
A member(s) who wishes to write a paper and publish it through OIX, should initially produce a synopsis of the intended paper and present it to the OIX Executive Committee. The Executive Committee will provide comment as to whether it believes it is suitable and relevant and, if not, offer informe...
A project report reflects the outcomes of a project. It is written by an author who should be appointed on commencement of a project.
A project report is published to an international community. It should be concise and written for a predominantly business-level readership. Industry jargon should be avoided. It is good practice to include a glossary.
Additional project material may be published alongside a project report. This may include techni...



